The Frighteningly True Cost of Ransomware Part 1
 You’ve heard the stories. You’ve seen the movies. Someone is abducted and held for ransom. From there the plot thickens and unfolds until, at last, the ransom is paid, the hostage is returned, and the criminals are caught.
You’ve heard the stories. You’ve seen the movies. Someone is abducted and held for ransom. From there the plot thickens and unfolds until, at last, the ransom is paid, the hostage is returned, and the criminals are caught.
However, by now you are beginning to understand that ransom in the 21st Century deals less with holding people hostage and more with blocking access to your computer and holding your data hostage.
Of course, that will never happen to you.
Or will it?
A Dose of Reality
People who think that they will never be attacked by ransomware are living in a fantasy world. Here is what is happening in the real world. Right here. Right now.
According to a report by Malwarebytes:
- Companies, large and small, are attacked by ransomware every 50 seconds.
- Individuals are attacked every 10 seconds.
- Total ransomware damage is expected to exceed $5 billion dollars this year.
- That’s $5,000,000,000.
- 60% of all malicious cyberattacks in 2017 were ransomware.
- Advertising fraud comprise another 20%.
- Download, backdoor, botnets, and all other forms of attack combined made up the additional 20%
- Ransomware variations have increased by 430% in the first quarter of 2017 compared to the same period in the previous year.
- One readily-available ransom software package releases new updates approximately every 8.4 days!
- 71% of companies targeted by ransomware have been infected.
- 72% of all businesses lost access to their data for 2 days or longer.
- 96% lost an entire day’s worth of data
- 61% lost 3 or more days’ worth
- 32% lost 5 or more days’ worth
- 66% of all ransomware attacks now use network file-sharing protocols to infect computers.
- These attacks do not require you or an employee to make an error in judgment.
- They simply attack weak passwords or other security points.
- 75% of corporate ransom attacks infect three or more employee workstations.
- 50% of corporate ransomware attacks infect at least 20 employee workstations.
- The most favored variant of ransomware spreads like an infection. Once it is in your system, it spreads from device to device.
A Warning of Things to Come
There is no apparent decline in ransomware attempts. There is no reason to expect that there will be. Consider these two facts which we will embellish in a following article:
1. Ransomware has become a lucrative cybercriminal business, garnering multiple millions of ill-gotten dollars. By “business” we mean central figures operating with affiliates who split the take.
2. Ransomware has attracted amateur wannabes. These people are more likely to get caught, but that does not lessen the degree to which they can inflict damage.
Tech Sentries works diligently to keep you aware of potential dangers and how to take a few, common-sense steps to Guard Your Technology and to ensure the safety of your data and devices.
Keep up to date with us as this series continues to unfold and to reveal the realities of ransomware – and what it could cost you and your business.
We are as concerned about your computer system security as you are. Your computer system security is our business. That’s why Tech Sentries is always on duty. Contact us today to learn how we can help you “Guard Your Technology” (843-282-2222).






 blocked.
blocked.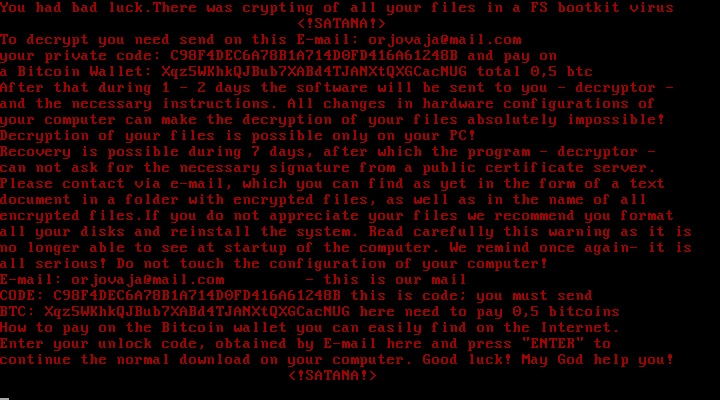

 virus gets in and the crisis starts.
virus gets in and the crisis starts.
 perpetrator! Hard to believe? Well, it gets worse. They send notices to you claiming that you have stolen bitcoins from them and that the only way they will leave you alone is if you pay them $33,000 USD to solve the matter. They claim to know a lot of your personal information and this, of course, lures people in simply by using the fear tactic. HOWEVER—this particular virus company has yet to actually collect any of this money, as most people aren’t going to give them the time of day once they see that amount! If you see anything at all with the name MIRCOP, close it, do NOT open any attachments, and just be aware of your activity.
perpetrator! Hard to believe? Well, it gets worse. They send notices to you claiming that you have stolen bitcoins from them and that the only way they will leave you alone is if you pay them $33,000 USD to solve the matter. They claim to know a lot of your personal information and this, of course, lures people in simply by using the fear tactic. HOWEVER—this particular virus company has yet to actually collect any of this money, as most people aren’t going to give them the time of day once they see that amount! If you see anything at all with the name MIRCOP, close it, do NOT open any attachments, and just be aware of your activity.