Why Old Methods Can’t Stop Ransomware
During the American Revolution, sentries guarding encampments reportedly shouted, “Halt! Who goes there? Friend or foe?” As far as we know, there are no statistics that indicate how many foes identified themselves as such – or lived to tell about it.
Ransomware is not easily identified
As of this time, conventional anti-virus software is about as effective at identifying ransomware as Revolutionary War sentry was at identifying friend or foe. We do have some statistics for the current day.
A recent survey of 500 companies found that
- 33% had been attacked by ransomware in the previous 12 months
- More than half of those companies were operating multiple anti-virus software at the time.
Think about that.
- Of 500 companies,165 had been attacked by ransomware
- Of those 165 attacked, 87 were employing multiple lines of defense.
That’s like having multiple perimeters of sentries, none of which would identify the foe.
There’s a reason for that.
The common approach is called blacklisting. Software already identified as “foe” is blacklisted. The problem is that the software cannot be identified as evil until it has permeated someone’s defense perimeter. Once identified as malware, conventional anti-virus publishes, in effect, “Wanted” posters so that computers can recognize software already known to be malicious.
There’s a solution for that
The solution is in implementing the opposite of blacklisting. Computer techies call it “whitelisting.” Instead of issuing wanted posters, a whitelisting approach allows only known friends to pass.
Pernicious thinkers amongst our readership might be thinking that ransomware can disguise itself by wearing someone else’s clothes. Not so. If ransomware producers think that they can masquerade as a friend, they will be sorely surprised to discover that they are wearing the proverbial Emperor’s New Clothes. The ruse will be discovered, and the attempt at ransom will fail.
Are you adequately protected against ransomware? Don’t think so. Know so. Contact us and let us show you how you can be sure that you are protected.




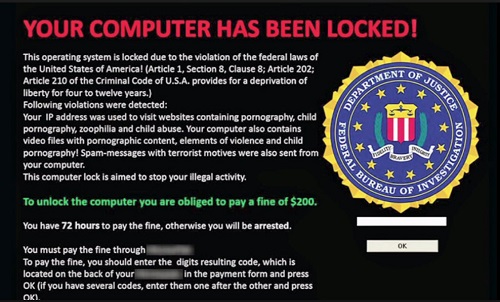


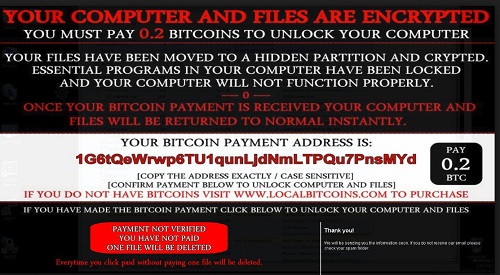

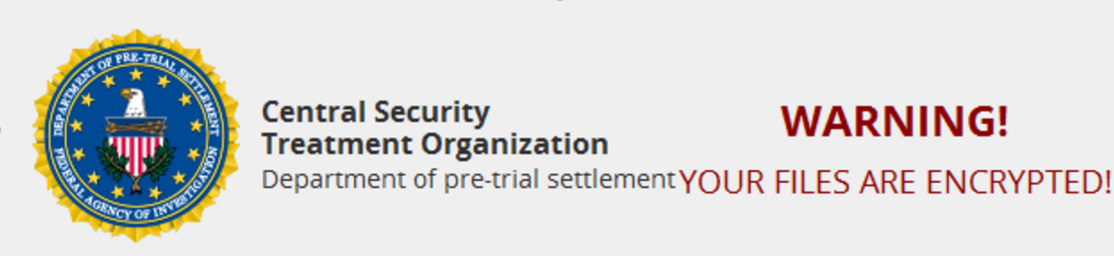



 After a relatively calm period, the researchers at Microsoft are warning that the
After a relatively calm period, the researchers at Microsoft are warning that the 



 We don’t know the motives of the perpetrators. Frankly, when you are the victim, the criminals’ motivations don’t matter. What matters is the damage that they have caused. Think of, for instance, a patient in the ER with a heart attack. The cause of the attack is relatively unimportant. What matters most is that the person can regain his health and that steps are taken to ensure that it doesn’t happen again.
We don’t know the motives of the perpetrators. Frankly, when you are the victim, the criminals’ motivations don’t matter. What matters is the damage that they have caused. Think of, for instance, a patient in the ER with a heart attack. The cause of the attack is relatively unimportant. What matters most is that the person can regain his health and that steps are taken to ensure that it doesn’t happen again.