Why Backups Aren’t Enough
Perfect backups will not always prevent the consequences of a ransomware attack, but backing up is vitally important.
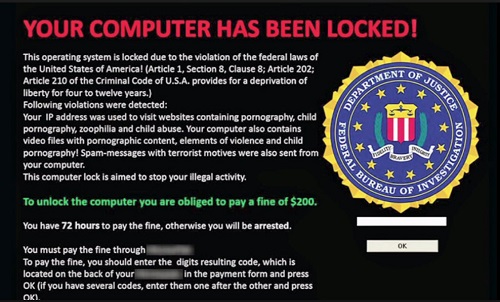
The Problem with Ransomware:
A high-profile ransomware attack hit a well-known transportation agency over a recent holiday weekend. This attack was a major eye-opening event, to say the least. For the first time, a major transportation agency has been shut down by a ransomware attack. To give you a few details, they estimated that approximately 900 of the computers in this agency were affected. They were using backups and this provided them with the ability to restore data with no intentions of paying the ransom; so one would assume all was well. Not exactly…
The transportation agency’s use of backups prevented them from losing all their customer and internal data. The use of a simple backup prevented a major catastrophe for this agency. Without the backups, they would have been faced with paying the ransom in this case, or been faced with heavy financial losses. It took approximately 2 to 3 days in order for most of the computers to be restored and the rest followed within the week. A large portion of their workforce was inaccessible for several days and some parts were down for almost an entire week.
The inability to work and work properly is going to cost any business money and valuable resources. With the transportation agency’s computers inaccessible, they had to shut down the terminals and payment systems, allowing the public to ride the metro for free. Many local articles stated that the systems being down was costing the agency $500K for every day that they were down and not working. This ransomware attack cost this transportation agency over a million dollars in the time they were down and not running. Backing up a system can save data and is very important, but many times it is not quick enough to get you back online without losing valuable time.
The Solution:
The story of the transportation agency demonstrates the vital importance of prevention when it comes to ransomware attacks. In order to eliminate this problem before it begins, it’s important to put your emphasis on prevention instead of detection and recovery. We believe that prevention is the only way to protect your business investment, and that is why we use global application whitelisting. Whitelisting allows you to avoid organized attacks and targeted areas because unknowns are always blocked no matter how new they are. We have no way of knowing what antivirus protection the agency was using, but even with their backups they suffered huge financials losses due to downtime.
Prevention is key! If you have any questions about ransomware attacks and how to keep your business protected, please give us a call at 843-282-2222 TODAY!













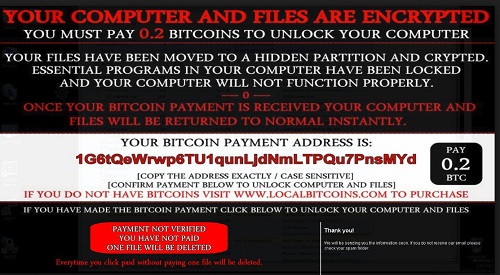



 After a relatively calm period, the researchers at Microsoft are warning that the
After a relatively calm period, the researchers at Microsoft are warning that the 
