To Activate or To Cancel: The Flash Play Malware Conundrum
Before you suffer Hamlet-esque paralysis by analysis, we want to warn you about a Trojan that is currently targeting Android users around the world. This especially insidious malware doesn’t care how long you look before you leap because you are darned if you activate or darned if you cancel.
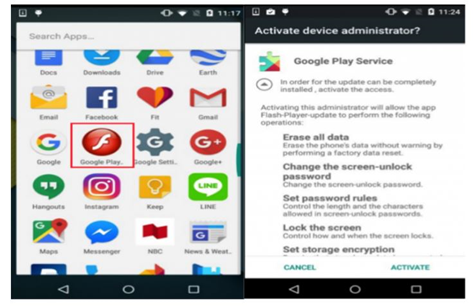
Gotcha!
Once the app appears on your Android device, it doesn’t matter what you do. You’ve already been had. Taking the form of an Adobe Flash Player app, a typical, but counterfeit, appears on your device and displays the options of “Activate Device Administrator” or “Cancel.”
If an unsuspecting user chooses “Activate,” the pop-up screen disappears, but the Trojan activates in the background and effectively gains total administrative rights on the device. Obviously, “Activate” would not be the wise choice.
The Obvious Answer is Wrong
Based on what we have shared so far, the obvious response would be to “Cancel.” Wrong. The “Cancel” option is another cleverly devised “Gotcha!” In fact, it may prove to be more frustrating than choosing “Activate.”
When you choose “Cancel” the pop-up screen disappears – just like you would expect it to. Momentarily. Then it reappears. No matter how many times you click “Cancel,” the pop-up keeps popping up. It won’t go away until you choose “Activate.”
But, Wait! There’s More!
A good criminal (Look folks! An oxymoron!) always has a backup plan. In this case, the malware has its own deletion prevention system built in. Imagine a bunch of cyber-thugs certified in virtual martial arts. This malware will not go away simply because you want it too and it already anticipates what you will do to get rid of it.
Houston, We Have a Problem
Like the Apollo 13 astronauts, we can be thankful that there is a way. It may look like duct tape and bailing wire, but who doesn’t love duct tape?
The Trojan can be manually removed by going to: Settings>Security>Device Administrators>Google Play Services>Deactivate. Once the administrative rights are deactivated, the user can find the Flash Player update and delete it.
The moral of the story is that sometimes you get stuck between a rock and a hard place. Often, there seems to be no way out. Sometimes the way out is not evident or easy. At Tech Sentry, it is our mission to protect you wherever we can and to rescue you when you need us. Contact us today to learn how we can help.









 Just when you thought it was safe in the water … Well, you know the rest of the story.
Just when you thought it was safe in the water … Well, you know the rest of the story.
 blocked.
blocked.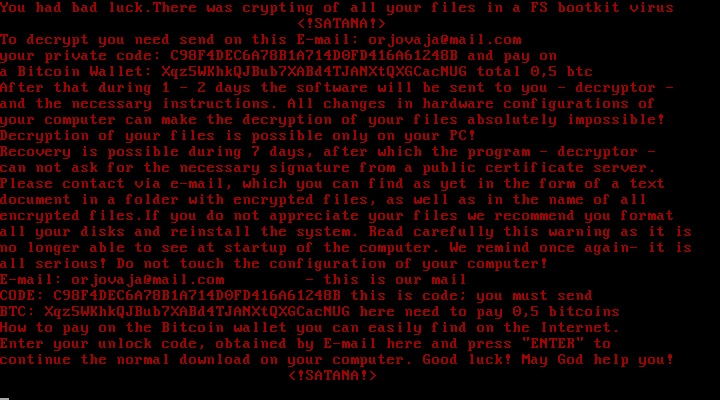

 virus gets in and the crisis starts.
virus gets in and the crisis starts.


 perpetrator! Hard to believe? Well, it gets worse. They send notices to you claiming that you have stolen bitcoins from them and that the only way they will leave you alone is if you pay them $33,000 USD to solve the matter. They claim to know a lot of your personal information and this, of course, lures people in simply by using the fear tactic. HOWEVER—this particular virus company has yet to actually collect any of this money, as most people aren’t going to give them the time of day once they see that amount! If you see anything at all with the name MIRCOP, close it, do NOT open any attachments, and just be aware of your activity.
perpetrator! Hard to believe? Well, it gets worse. They send notices to you claiming that you have stolen bitcoins from them and that the only way they will leave you alone is if you pay them $33,000 USD to solve the matter. They claim to know a lot of your personal information and this, of course, lures people in simply by using the fear tactic. HOWEVER—this particular virus company has yet to actually collect any of this money, as most people aren’t going to give them the time of day once they see that amount! If you see anything at all with the name MIRCOP, close it, do NOT open any attachments, and just be aware of your activity.
 software programs where they spread and multiply. They are almost always there due to nefarious intent. It can be hard to know when and if you’ve been infected by computer viruses, so you need to know the symptoms to look for. They include lost space on your hard drive, data that becomes corrupted, pop-ups that are relentless, and personal information that becomes compromised.
software programs where they spread and multiply. They are almost always there due to nefarious intent. It can be hard to know when and if you’ve been infected by computer viruses, so you need to know the symptoms to look for. They include lost space on your hard drive, data that becomes corrupted, pop-ups that are relentless, and personal information that becomes compromised.