Chances are, you have found yourself in this predicament before:
You turn your computer on, wait for what seems like an eternity for it to boot up. When it finally does, your programs are slow to start, your internet is sluggish and your cursor is delayed several seconds behind the mouse. If this has happened to you, your first thought might be to reboot because you have too many things running at once. The more likely scenario is that you’re infected with a malware virus. While they can sometimes be fairly obvious to spot, malware can also hide really well. You’ll have to do a little searching to see how sick your computer is and how best to treat it so it can be totally cured.
How Do You Know If you’re infected by malware?
Well, the first sign of being infected is for your computer to wig out. It may act really strangely and sometimes it’s obvious, but other times it’s not. It helps to understand the symptoms that can happen so you’ll know what to look for. Here are some other symptoms and problems:
Ransomware
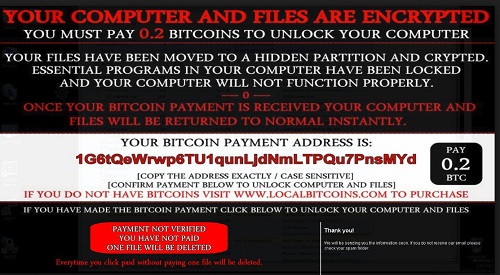
People who author ransomware actually want it to be crystal clear that they have infected your computer. They make a lot of money doing it and if you’ve been infected, you’ll most likely see pop-up windows with messages about your files now being encrypted. They will also usually demand a ransom by a certain deadline in order to restore your files.
Your Browser Constantly Redirects Someplace Else
Perhaps you do a search in Google for something. You choose a link to click on, only to be redirected to a different page. You’ll most likely hit the back button and choose another link to click on, only to have the same thing happen. This is a classic infection of malware.
Different Home Page
You set a custom home page but it won’t come up. Instead of the page you’ve set, a totally different page appears when you open your browser. Also, you may notice a row of toolbars under your browser that you don’t recognize. It may be impossible to get rid of these icons. This can be another classic malware infection.
Constant Pop-Ups
By constant, we mean constant! If you close one only to have one more come up, or you’re getting pop-up ads when you’re not even online, you’ve likely been infected.
Signs of Malware That Are Less Obvious
Computer is running too slow. This could be everything from too many programs active, to being low on space or memory. It could also be malware.
Icons you don’t recognize. It’s possible to get these icons from several sources, such as someone downloading a program or game without your knowledge, or even when you download software and a PUP (potentially unwanted program) comes along with it.
Crashing Constantly. Again, there can be many causes for crashing, but if it happens all the time or only with certain programs being opened, it’s likely you’re infected with malware. A professional can diagnose this.
Your browser freezes. If your browser becomes unresponsive, it could be nothing more than a slow or bogged down internet. Your internet provider can help you check your download speeds. If everything looks good, malware is a definite possibility.
A few other signs can include:
* Multiple bounced emails
* Battery dying too fast
* Bills that are larger than normal
Finally, it’s possible to get malware infections with absolutely no sign at all! The best way to avoid malware altogether is to have Tech Sentries keep you protected. We test constantly for computer viruses and can stop them before they create major issues. Tech Sentries can keep you safe in the background automatically so you can go about your business with confidence. If you have been infected, we will help you rectify and restore your computer to its original state.
Remember, the hackers are always inventing new ways to infect your computer. Tech Sentries stays on top of it so you don’t have to!
Call us today at 843-282-2222.






 Keeping others from being able to see the content on your computer is your right. No justification is needed—only appropriate action. In today’s political climate, computer security is one of the most common questions we are asked here at Tech Sentries. These questions often deal with protecting your data, keeping the government out of your affairs, and even encryption. If you don’t know what encryption means, much less how it’s used, this article is for you!
Keeping others from being able to see the content on your computer is your right. No justification is needed—only appropriate action. In today’s political climate, computer security is one of the most common questions we are asked here at Tech Sentries. These questions often deal with protecting your data, keeping the government out of your affairs, and even encryption. If you don’t know what encryption means, much less how it’s used, this article is for you!
 After a relatively calm period, the researchers at Microsoft are warning that the
After a relatively calm period, the researchers at Microsoft are warning that the 
 How long a cyberattack remains a headline depends on the next major story that breaks. That’s just the nature of things. An attack happens, followed by headlines and hoopla, then most everyone moves on.
How long a cyberattack remains a headline depends on the next major story that breaks. That’s just the nature of things. An attack happens, followed by headlines and hoopla, then most everyone moves on.




 Did you know that elderly people aren’t necessarily the most likely to be scammed online? Well, the Better Business Bureau issued a report stating that its Millennials and Generation X’ers who are the most likely to be a victim of scammers. The reason? The elderly population are far more likely to actually report the incident of a scam before financial loss occurs. In fact, over 90% of them will report it sooner than the younger generation. Even though Millennials and Generation X’ers are far more tech savvy, they are far slower to report being scammed, making them much more likely to lose money as a result.
Did you know that elderly people aren’t necessarily the most likely to be scammed online? Well, the Better Business Bureau issued a report stating that its Millennials and Generation X’ers who are the most likely to be a victim of scammers. The reason? The elderly population are far more likely to actually report the incident of a scam before financial loss occurs. In fact, over 90% of them will report it sooner than the younger generation. Even though Millennials and Generation X’ers are far more tech savvy, they are far slower to report being scammed, making them much more likely to lose money as a result.
 Have you ever heard of
Have you ever heard of 
