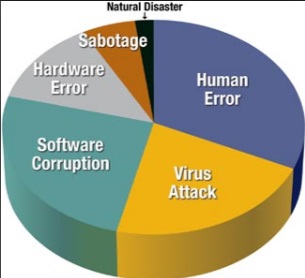
Top Ten Computer Problems Your IT Specialist Can Fix Remotely
 Remote IT support has come a long way, with many IT issues able to be solved without having the device in hand. An IT technician can usually speak with the user and handle most issues remotely. This means you don’t have to live in the same city as the IT expert. It also means that they must be able to handle a host of issues quickly and efficiently. Gone are the days where the user had to be guided step by step by the expert. Logins and desktops can be accessed remotely, making computer repair easier than ever.
Remote IT support has come a long way, with many IT issues able to be solved without having the device in hand. An IT technician can usually speak with the user and handle most issues remotely. This means you don’t have to live in the same city as the IT expert. It also means that they must be able to handle a host of issues quickly and efficiently. Gone are the days where the user had to be guided step by step by the expert. Logins and desktops can be accessed remotely, making computer repair easier than ever.
While remote IT repair has indeed come a long way, it can’t fix everything. There are some problems such as networks, printer issues or peripherals, that must be fixed in person. Read on to see the top ten issues that can be fixed remotely!
- Windows Blue Screen of Death (BSOD). This is a scary problem to most users and usually the assumption is made there is no coming back from the blue screen. However, it doesn’t always mean that you need a whole new set of hardware. Often, simple things like updating Windows or replacing a driver can solve the blue screen horror.
- Can’t Connect to the Internet. Believe it or not, this is usually a very easy fix. More often than not, it’s an unplugged cable or a locked-up router. A tech can remotely login to your system and with the assistance of a person on the other end, have it resolved quickly.
- Can’t Log In. Most of the time, this too can be solved remotely. Something as simple as cap lock being on or a cable being loose is often all it is. Sometimes the problem is a little deeper, such as an Active Directory problem or a profile that has become corrupt. All of these problems can be addressed remotely.
- Accidentally Deleting Files. This one is by far the most common issue IT techs face. The biggest thing to stress here is GET A BACKUP plan! It’s always better to plan ahead before a problem happens. Tech Sentries has the best backup available. Having said that, it is possible in some cases to retrieve deleted files. Even so, you should perform backups on a regular basis.
- Computer Running Slowly. This is a big one. We see these calls all the time and it can make for a very frustrated user. Most of the time, a good cleaning of the computer’s files and functions will solve this problem. It could also be malware that needs to be removed, a failed update that got stuck running in the background, or even a faulty app. These issues can all be resolved remotely.
- Random Rebooting. If you’ve ever dealt with this, you already know it can be maddening! Often, your work is lost if the computer reboots itself randomly so it’s crucial to get this repaired. Good news is that your IT specialist can usually fix this remotely.
- The Network Printer Won’t Print. It’s hard to say why this happens sometimes, but it can usually be fixed remotely. It could be un unplugged cable or toners and cartridges that ran dry. Even if it’s a configuration issue. Network printer problems are usually easily solved.
- Slow Internet. The internet can get boggy when too many people are using it with incorrect configurations. While it could be a virus or other malware, a slow running internet is often fixed simply by rebooting and reconfiguring the router, which be done by your IT specialist remotely.
- Wi-FI Network Randomly Dropping Devices. Most of the times, this problem is a configuration issue. Sometimes exterior problems such as super thick walls or a lot of metal all around can be the culprit. Unfortunately, we can’t solve these issues. But, most other Wi-Fi connectivity problems can easily be fix on a remote basis.
- Frozen Computer. Although you don’t usually need professional IT help for a frozen computer, it’s one of the most common calls that come in. If this happens to you, unplug the computer for a few minutes and reboot. If it continues freezing up on you, an IT specialist can log in once it’s up and running again and diagnose the problem. It can be challenging to fix this issue remotely, but not impossible.
No matter how great your computer is, you should always have a relationship with an IT support team. Whether it’s proper backup or major computer repair, Tech Sentries is the best in the business! Call Tech Sentries today! (843) 282-2222.










 Increased awareness is taking place concerning a phishing attack. It has been around for over a year and is targeting Gmail users. Inboxes are being infiltrated by hackers, which is allowing these cyber criminals access to both incoming and outgoing email messages. That in and of itself isn’t the shocker. What is more surprising is what happens next. Hackers look for emails that have links attached and replace them with a Gmail login screen that is malicious. Once the user clicks on the attachment, they will see a Gmail login screen prompting the login and password for that account. Once this happens, the hackers have instant access to sensitive login information, making it easy for them to see a whole new inbox to start the process over from.
Increased awareness is taking place concerning a phishing attack. It has been around for over a year and is targeting Gmail users. Inboxes are being infiltrated by hackers, which is allowing these cyber criminals access to both incoming and outgoing email messages. That in and of itself isn’t the shocker. What is more surprising is what happens next. Hackers look for emails that have links attached and replace them with a Gmail login screen that is malicious. Once the user clicks on the attachment, they will see a Gmail login screen prompting the login and password for that account. Once this happens, the hackers have instant access to sensitive login information, making it easy for them to see a whole new inbox to start the process over from.